
Are you analyzing malware? Do you encounter malware that expands to a huge file size, like 600-800+ MB, from a mere 5-10 MB after unzipping it? Maybe you are scratching your head about what to do next since you can't upload it to your automated malware sandboxes? Don't worry, I've got you covered with some tricks that will help you debloat/unpad the malicious file, making your task of analyzing it easier! :)
What is a Inflated/Bloated/Padded PE File?
PE files are artificially padded/inflated/bloated by adding an overlay of zeros (0's) to the PE file which in turn increases the file size of PE.
This tactic is generally used by malware authors to evade detection of malicious payloads by AV and EDR engines. These kinds of large files are also not supported by automated sandbox services like VMRay, CS Falcon, Intezer, VirusTotal, and JoeSandbox, as there is an upload file size limit.
e.g. The original malicious file is of 1 mb. A threat actor pads this file by adding zeros (0's) to the executable which increases the file size to 700 mb. If you try to upload it to popular automated sandboxes, you'll be faced with an error saying file size too large to upload!
Why Inflate/Bloat/Pad a PE file?
Binary padding is a common technique listed in MITRE as T1027.001
There are several reasons for which malware authors do this:
Padding does not change the functioning or behaviour of the binary.
When the padded binary is executed, it automatically ignores the padding or zero's
Padding changes the hash of the file!
Even a single zero added to the file will change it
This will help the file avoid file signature based AV detection engines. A pretty cool way to stay under the radar :)
Will avoid any file-hash blocklists and just execute defeating traditional security controls!
It helps the file/malware evade automated sandboxed which hinder the file from being analyzed due to file upload size limitation
Effective on all OS including
macOS
Linux
Windows
How to detect if the PE file is Inflated/Bloated/Padded?
There are several methods a malware analyst uses. Here are 4 of them:
The first indicator is a unsually high file size which is instantly recognized.
Using DIE or Detect It Easy
Drag and drop the file to DIE
Click on Overlay
You will see a lot of zeros (0's). This means the file has been inflated


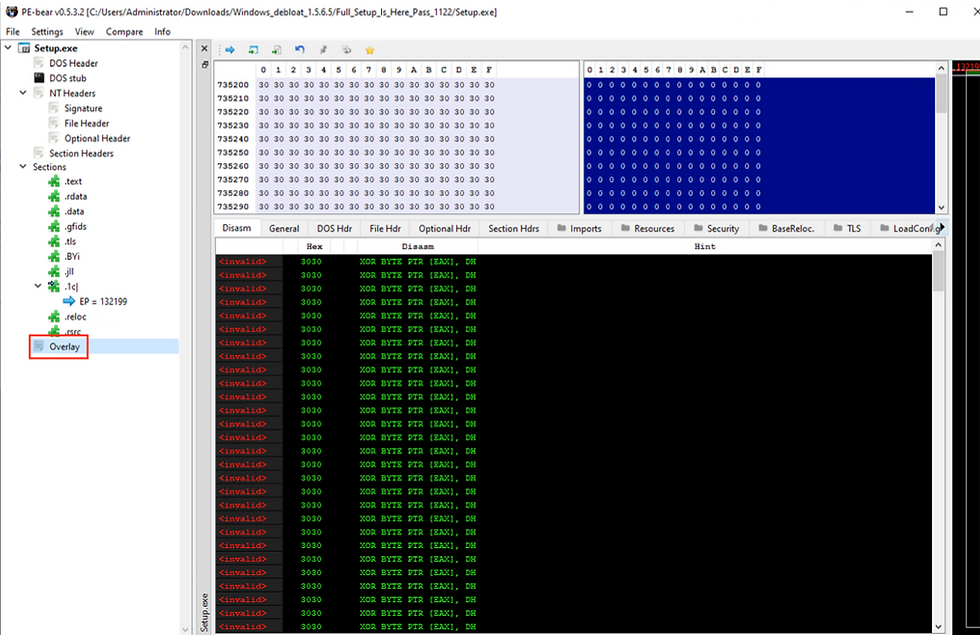
Using PE-bear
Drag and drop the file into PE-bear
If an Overlay is present it will be shown at the end
When clicked on it, a lot of zeros (0's) can be observed
Using pestudio
Drag and drop the file into pestudio
Wait for sometime to auto parse and detect the overlay.
If you see overlay (n/a), it means there is no overlay present in the PE

How to remove Overlay from Artificially Inflated/Bloated/Padded PE Files?
There are 2 methods to remove overlay:
Manual
Automated/Tool based
Let's explore both!
1] Manual method:
I used to do this when I didn't know any tools or scripts existed! I know it was a lot of wasted time, but it's a learning nevertheless :)
Using any Hex Editor
Open the padded file using Hex Editor like HxD or 010 Editor
Scroll down a bit and you will see a lot of 0's which is intentonal garbage put in the executable to inflate or increase the file size
Remove the zeros (0's) manually and save the file. This is an extremely time consuming process and you will end up scrolling a lot! Have some patience :)
Another method is to check for the offset value of the garbage values of zero's (0's) from pestudio, Detect It Easy or PE-bear. These tools will show you start and end offset values. So once you know it, go to your hex editor and jump to the start offset and select it till the end of the offset value you previously saw, delete the selected block of data containing zeros and save the file.
Tip: Keep some zeros (0's) to make sure you don't end up with a corrupted executable which won't execute during dynamic analysis!
Reference:

Checking Inflated PE file with a lot of 0's using a Hex Editor
2] Automated/Tool based method:
Using Debloat
Pros:
Debloat is a GUI tool (Debloat
Cross-platform working
Works on OS's like
Windows
macOS (Works on both Intel and ARM machines!)
Linux
You can even use it via CLI
After installing using pip install debloat use the command debloat
Steps:
Download the Debloat tool on your Malware Analysis Sandbox
Extract the zip
Open the debloat executable
Drag and drop the inflated file on the text bar and click on Process file.
Once the processing is completed it will give Processing complete result and create a file with filename_patched.exe


Using pecheck.py
This is a CLI tool written by Dider Stevens!
Reference
Prerequisites:
Python
Steps:
Download from pecheck.py
Extract pecheck.zip
Make sure that the inflated file is located in the same location as pecheck.py
Open command prompt as Administrator mode
Use the below command and wait for some time for the stripped file to be generated
pecheck.py -g s -D <Inflated file.exe> > <Desired filename.exe>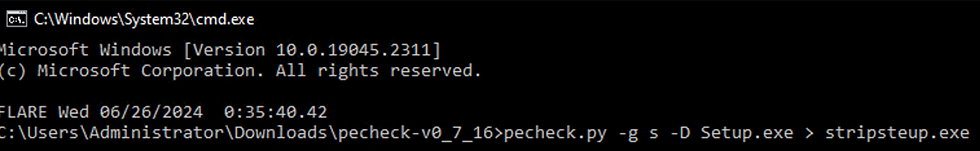
Caveat with removing overlay/padding:
Legitimate applications contain an overlay that is relatively small. If you remove it, your software might break and won't work. So if you're dealing with a suspicious file and see some zeros (0's), don't go ahead and remove all of it. Keep some smaller part of the overlay so that you don't end up breaking the file for execution/dynamic analysis.
Sometimes, the overlay may consist of random characters or just a blob of ones (1's) or twos (2's). This can make detection of it very hard, and your tools will end up being useless. In this case, you would have to switch back to the manual method of removing it!
